Chris Schreiber
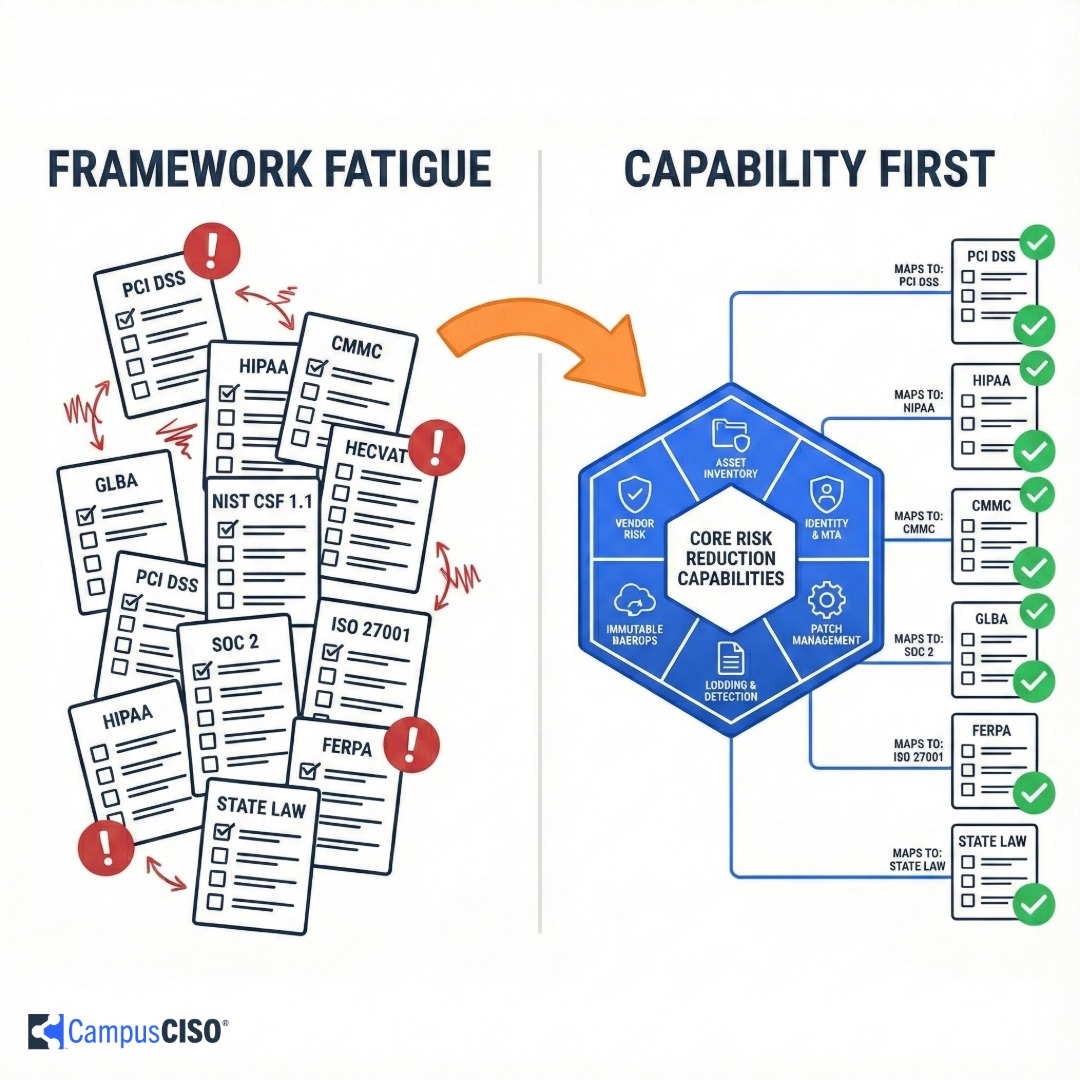
Discover how higher-education security leaders can escape “framework fatigue” by adopting a capability-first, framework-agnostic strategy. This approach prioritizes core controls that cut risk campus-wide, then maps evidence back to PCI DSS, HIPAA, CMMC, GLBA, and future mandates—slashing audit overhead while strengthening real-world resilience.
Your university operates in a regulatory thicket denser than almost any other industry. You’re simultaneously a bank processing tuition payments, a healthcare provider running clinics, a defense contractor managing federal grants, and a municipal utility operating critical infrastructure, all under one institutional umbrella.
This unique position creates an overwhelming compliance burden. Each framework speaks its own language, demands specific evidence, and drives your security roadmap in different directions.
The result? “Framework fatigue” where your security strategy becomes dictated by the next audit finding rather than by actual risk reduction.
There’s a better approach. By building a capability-focused security program first and mapping to frameworks second, you can break free from the compliance treadmill while strengthening your actual security posture.
A single research university must comply with PCI DSS for credit card transactions, HIPAA for campus health centers, CMMC for Defense Department grants, and export controls for research. Add federal student aid rules (GLBA Safeguards), state data breach laws, and sector-specific frameworks like HECVAT, and compliance becomes a full-time job.
Each framework uses different terminology for similar controls. Auditors demand one-to-one mappings and unique evidence for each requirement, creating redundant work for already stretched teams.
Security leaders end up debating which spreadsheet column to populate instead of how to address material security gaps. Your roadmap becomes driven by compliance deadlines rather than by what actually reduces risk.
According to a study by Ponemon Institute and Globalscape, the average cost of non-compliance runs 2.7× higher than compliance, making an efficient approach critical for resource-constrained institutions. Read the full study.
A framework-agnostic strategy changes the conversation from “Which checklist do we chase next?” to “Which core capabilities reduce risk across our entire campus?”
Start by inventorying your security capabilities without reference to any specific rulebook. Once you’ve identified strengths and gaps, build a prioritized roadmap that maximizes your limited resources.
Because most frameworks describe the same fundamental safeguards in different ways, you can cross-walk your roadmap to any auditor’s rubric rather than rebuilding your program for each audit.
This capability-first model not only streamlines compliance but keeps strategy in your hands. This ensures every control serves an explicit risk-reduction purpose long before a regulator asks for proof.
Start with a rapid capability baseline using the Cyber Heat Map engine or the free NIST Cybersecurity Framework 2.0 Implementation Tier worksheet. Access NIST resources.
In just a few hours, you can rate each CSF Function (Identify, Protect, Detect, Respond, Recover) and surface high-risk gaps.
Focus improvement efforts where baseline data indicates your greatest need.
Leaders building their improvement roadmap should prioritize capabilities mitigating broad risk categories, such as:
Continually update your assessment results, recalculating priorities as you deploy new tools or complete training. This provides a living roadmap rather than a static report that quickly becomes outdated.
Successful institutions treat security as a capacity-building program rather than an endless series of projects. Build a firm foundation across every domain before adding specialized tools.
Run each proposed initiative through two tests:
Virginia Tech’s IT Compliance Manager Ryan Orren emphasizes this cross-framework approach: “The CIS controls will always be our core, but as other frameworks become relevant—like NIST 800-171 for CMMC and GLBA—it’s important to have a crosswalk between controls so we can demonstrate compliance.” Read the full article.
By prioritizing high-leverage improvements that support multiple compliance controls, you create a resilient foundation that auditors can trace back to their own checklists. All without derailing your strategic roadmap every time a new regulation appears.
When the FTC released its expanded GLBA Safeguards Rule in 2021, one research university we work with sidestepped the usual “GLBA fire drill” by completing a capability assessment.
The assessment highlighted already-planned projects that aligned with both GLBA and NIST CSF objectives: a comprehensive asset inventory, stronger vendor oversight, and a tested incident-response plan.
Instead of launching multiple GLBA compliance remediation efforts, they funded a few high-impact improvements: deploy an authoritative CMDB with automated discovery, embed third-party risk questionnaires in contract workflows, and schedule annual tabletop exercises.
This unified program advanced multiple CSF targets, satisfied several GLBA controls, and improved asset tracking required for future audits. All for a cost that fits within their existing security budget and support staff resources.
When audit season arrived, the CIO presented a living dashboard showing their progress and planned projects rather than a static binder. Auditors accepted the cross-walk and project as evidence for their risk assessments, and the board saw a coherent, resource-conscious roadmap instead of an expensive list of reactive fixes.
The first hurdle is cultural: auditors, finance officers, and IT teams are conditioned to treat every audit gap as an emergency.
When proposing a capability-first roadmap, some stakeholders fear that “ignoring” a finding, even briefly, puts the institution at legal risk. The antidote is data-driven transparency.
Start every conversation with a single slide or dashboard that ranks all open gaps by risk reduction versus cost. Show where each audit comment sits on that list and why a higher-impact item may take precedence.
Frame your plan as good stewardship of limited resources. This transforms “We’re saying no” into “We’re investing where the evidence shows the greatest benefit.”
A second challenge is ensuring stakeholders are comfortable with the evidence from your program. Auditors expect one-to-one control matrices; leadership worries that a framework-agnostic report won’t “check the box.”
Provide a cross-walk that maps each roadmap item to every relevant standard. The Cyber Heat Map platform can help generate this type or report automatically, clarifying that you can satisfy multiple frameworks with your planned projects.
Finally, prevent “analysis paralysis” by time-boxing decisions. Agree that you’ll refresh the roadmap quarterly and that only new threat intelligence or major incidents will reopen prioritization discussions.
Institutions that adopt a capability-first, framework-agnostic program consistently report three measurable benefits:
1. Fewer emergency projects and more transparent budgeting
Universities with a single, risk-ranked roadmap cut “audit-driven” fire-drills. The system triages every new finding against existing priorities.
This frees staff hours for planned work and helps finance teams forecast spending instead of approving surprise requests.
2. Lower compliance overhead
Because one improvement project produces evidence for to support several standards, teams spend less time on documentation and audit-prep work.
3. Measurable risk reduction that resonates with leadership
With live scoring and benchmarking, you can show year-over-year capability gains and tie them to reduced exposure.
IBM’s data puts the average higher ransomware recovery at $4.02M. Institutions using a unified roadmap can show how closing high-impact gaps lowers that liability, turning security spending into an easily explained return on risk.
Step 1 – Secure executive sponsorship and reset the narrative
Begin with an executive-level statement that your institution is moving to a capability-first model grounded in risk reduction, not checklist completion. Explain this decision to auditors, IT directors, and finance so everyone understands how you’ll set priorities.
Step 2 – Establish a data-driven baseline
Run a rapid NIST CSF self-assessment or Cyber Heat Map survey to score each core function and reveal the largest risk-versus-cost gaps. Publish the results, warts and all, so stakeholders see the same evidence.
Step 3 – Engage the right partners
Pair internal talent with a strategic partner or community of practice to validate scoring, share playbooks, and keep local bias from warping priorities.
Step 4 – Involve every technology domain owner
Hold a working session where security, infrastructure, network, cloud, and application leads work together to assess your current capabilities and identify potential improvement priorities. This prevents siloed wish lists and secures shared accountability.
Step 5 – Commit to an iterative, living roadmap
Lock the first 90-day action plan, schedule quarterly refreshes, and tie budget requests (across ALL technology groups) to the current top five gaps. A cadence of small, visible wins builds momentum and prevents backsliding into audit-driven fire drills.
Peer collaboration multiplies your scarce resources and brings real-world evidence to your roadmap. Higher education professional networks, research partnerships, and shared service staff already connect campuses; transparent security dialogue strengthens everyone’s posture.
Join trusted communities like EDUCAUSE’s Cybersecurity & Privacy Community Group for discussion lists, surveys, and template repositories.
REN-ISAC provides daily threat intelligence and vetted peer briefings under an MOU that protects confidentiality while enabling frank information exchange.
Move beyond talk by swapping playbooks, tabletop scenarios, and control mappings. Private alliances like Cyber Bridge let institutions trade documents and lessons learned in a members-only space.
Use benchmarking data to help justify funding. Presenting “we’re in the bottom quartile for asset inventory” turns an abstract gap into a quantifiable risk and a compelling budget request.
Framework-agnostic programs become more valuable as regulations multiply. Recent developments include NIST CSF 2.0 and its “Govern” function, the DoD’s final CMMC rule, SEC breach-disclosure regulations, and NIST’s first post-quantum encryption standards.
To stay ahead of these changes:
By treating your capability model as the center of gravity instead of an individual framework, you can absorb new regulations with a change to the mapping layer, not a rewrite of your program.
The fundamentals don’t change with institution size, but implementation strategies should.
Smaller colleges should pursue breadth before depth. Use lightweight, cloud-delivered tools and assign cross-functional “security champions” rather than hiring specialists. Focus on the single highest risk-reduction project in each budget cycle.
Large research universities need more depth and advanced features. After establishing solid foundations, add domain-specific layers: privileged-access management for HPC clusters, automated vendor-risk platforms for thousands of sub-awards, or 24×7 SOC monitoring.
Always apply an ROI lens that reviews impact on risk and compliance versus total cost to deploy and sustain. This matters to institutions regardless of size; large budgets vanish as fast as small ones.
The framework-agnostic approach transforms cybersecurity from an endless series of compliance remediation projects into a strategic advantage for your institution.
By focusing first on capabilities that reduce risk, then mapping those capabilities to frameworks, you can:
The question isn’t whether your institution can afford this approach. It’s whether you can afford to continue with the inefficient status quo of chasing frameworks one by one.
Start your journey today with the 30-Day Strategy Sprint. Map your current security state, identify your highest-impact gaps, and build a roadmap that delivers real security improvements while satisfying compliance requirements along the way.
Your future self, and your institution’s board, auditors, and security team, will thank you.

Start Your 30‑Day Diagnostic - $399
Build a data‑informed, board‑ready cybersecurity plan in 30 days.
Includes expert guidance, 30‑day access to the Cyber Heat Map® platform, and weekly group strategy sessions.
No long‑term commitment. Just results.
Secure your seat today.