Chris Schreiber
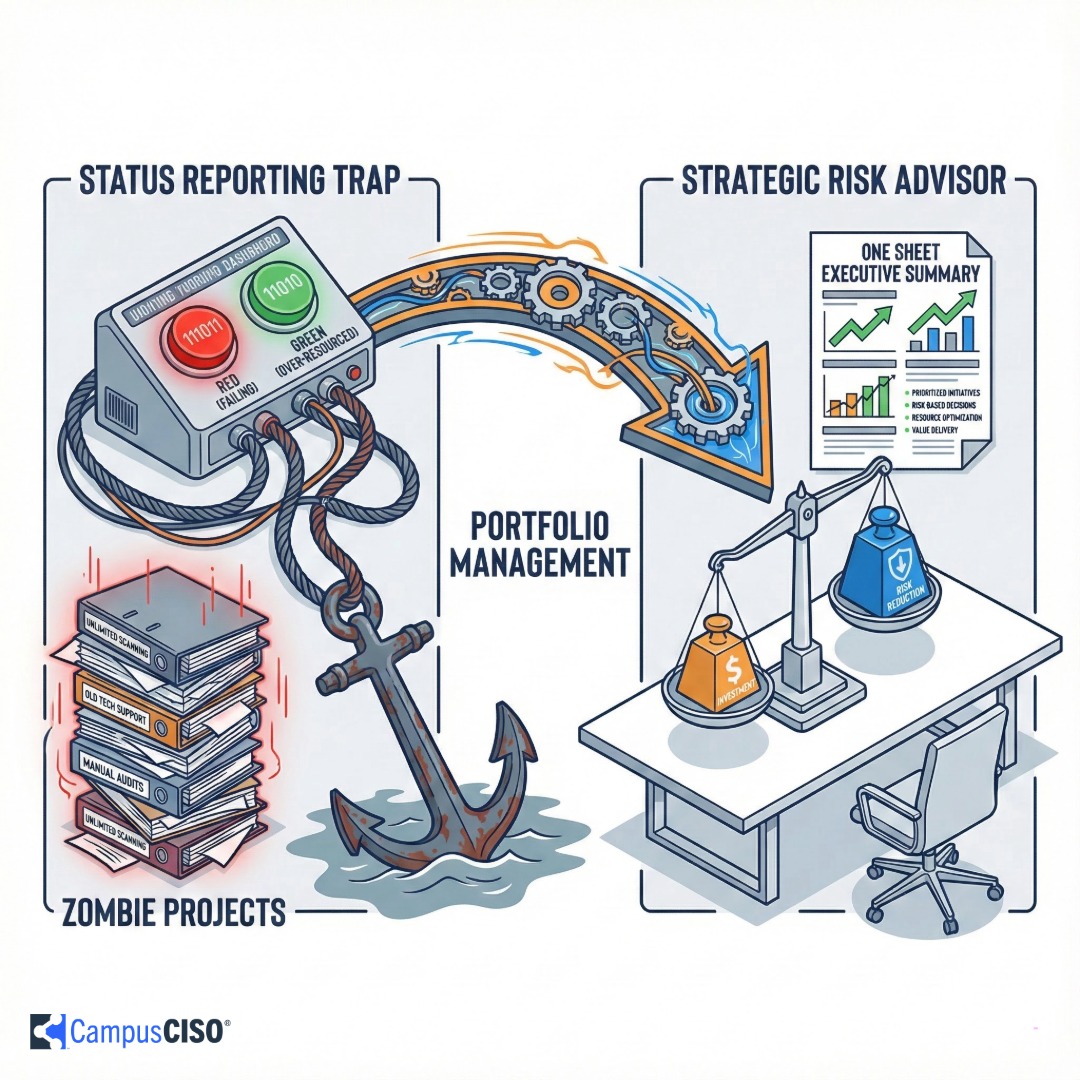
The "Traffic Light Trap" forces CISOs into a losing game: green dashboards signal you're over-resourced, while red ones signal incompetence. This article shows higher education security leaders how to escape by shifting from status reporting to portfolio management, using real-world examples, current industry data, and a practical framework for killing zombie projects, reducing burnout, and earning a seat at the strategic table.
The CISO walked into the steering committee meeting confident. Her team had spent weeks getting the compliance dashboard to green. 100% compliance on the metrics requested for the annual audit.
She expected relief. Maybe even recognition.
Instead, the CFO leaned forward and asked, "If everything is green, why are you asking for another analyst position?"
The room went quiet. Instead of celebrating success, she had walked into a budget freeze.
This wasn't a one-time mistake. It's a career-limiting pattern that keeps CISOs stuck reporting status instead of managing risk, and the pressure shows: average CISO tenure is now half that of other C-suite roles.
This is the Traffic Light Trap. When you report on status rather than risk, you create a binary outcome where you lose either way.
"Green" signals that you're over-resourced or "done" implementing security. "Red" signals that you're failing or incompetent.
The data proves this trap is tightening. Security budget growth has slowed to just 4% in 2025, the lowest rate in five years. This forces CISOs into a dangerous boom/bust cycle where funding only flows after a crisis turns the dashboard red.
That planning meeting taught me that compliance is a ceiling for your budget, not a floor. To break the cycle, I had to stop reporting on status (are we safe?) and start reporting on portfolio value (are we efficient?).
Ask yourself: Can you walk into your next board meeting and explain which three security projects deliver the most risk reduction per dollar spent? If not, you're still trapped.
The difference is that ROI tries to prove a negative (money saved by not getting hacked), while portfolio value shows efficiency (risk reduced per dollar spent).
ROI is fiction. Portfolio value is leverage.
When you present a portfolio view, you're not asking the board to believe a made-up number about "future loss avoidance." You are asking them to make a resource allocation decision based on relative impact.
You're saying: "We have $1. We can spend it on Project A (high impact) or Project B (low impact). Here's the evidence of why A wins."
This approach allows you to do the one thing traditional security planning approaches almost never accomplish: kill zombie projects.
The average enterprise has assembled between 70 and 130 different cybersecurity products to protect its infrastructure.
In 2024, the number of published vulnerabilities hit a record high of 40,000+. This volume makes "scan and fix everything" a mathematical impossibility.
If you can walk into a board meeting and say, "We're retiring three underperforming tools to fund this one high-impact initiative without asking for a budget increase," you stop being a cost center and start being a portfolio manager.
That's the language of business.
"We're retiring three underperforming tools to fund this one high-impact initiative without asking for a budget increase."
This sentence transforms you from cost center to portfolio manager.
The zombie was a "Universal Vulnerability Scanning" policy at a large research university. On paper, it looked responsible: scan every website, fix every bug.
In reality, it was a hallucination. It demanded we treat a professor's personal blog running under a desk with the same rigor as the enterprise ERP.
An auditor fought to keep it because it was a clear binary rule to measure and report to the board.
Instead of killing it with logic, I killed it with a price tag.
I solicited an outside bid to execute the policy exactly as written. The vendor called a few days later:
“We're at $1 million per year and haven't scoped 20% of your network.”
I asked them to put that number on letterhead. That document ended the debate.
We replaced the zombie with a risk-tiered website registration process. We stopped wasting budget on low-risk findings and focused on problems that could cause material financial harm.
Being new to the role gave me the political cover to ask "why" we were trying to implement the website scanning project, but the motivation came from seeing the opportunity cost.
I wasn’t just killing a project. I was trying to reclaim my team's capacity.
Every hour my engineers spent scanning professor blogs was an hour they were not securing the identity systems that controlled access to our financial and research data.
The zombie project persisted because it was measurable, not because it was meaningful. The auditor loved it because "100% scanned" is a binary metric that fits on a presentation slide. My team hated it because they knew it was security theater.
Recent data shows that 47% of compliance professionals focus on "alleviating the burden" of requirements, while only 16% have shifted to a strategic approach.
When leadership attention focuses on a "traffic light" metric, that metric becomes the de facto strategy. My job was not to execute a poor strategy. I had to change the focal point.
By putting a $1 million price tag on the auditor's request, I forced a governance choice: did the institution want to pay for the checkbox, or did they want to trust experts to help manage risk more strategically?
Killing zombie projects is not just about budget efficiency. It is about team survival.
I sat down with the analyst coordinating the website scans and was honest: "This project is going away. But your value to this team is not defined by this project."
We mapped their institutional knowledge to a new gap: Third-Party Risk Management (TPRM). They knew every department IT manager, every data owner, and how to navigate the university's bureaucracy. Skills that are impossible to hire for.
By shifting them from a dedicated "website scanning coordinator" to "vendor risk analyst," we didn't just save a job. We solved a critical capability gap without opening a requisition.
When you remove low-value drudgery, you don’t just save budget. You save your people.
That analyst went from being the "scanning police" everyone avoided to a strategic partner helping departments buy software safely.
The CISO may own the breach response, but the CFO owns the checkbook, and the CIO owns the technology infrastructure.
The only way to escape Accountability Asymmetry is to pivot from "gatekeeper" to "advisor."
You can't force the university to buy a new identity system. But you can convene a governance committee to review options and sign off on the risk of not upgrading it.
Clear prioritization helps make your evaluation and decision process transparent. When you present a ranked list of "Next Best Moves" for security, you're effectively saying: "If we have $X and this many headcount, here's how far we can progress on managing our risk."
This moves the "bag" from your shoulders to the risk register and governance process.
The data proves this pivot pays off. "Strategic CISOs" who excel at C-suite engagement and aligning security with business goals earn 57% more than their technical peers.
Why? Because they don’t just fix problems. They help the institution manage risk and liability.
When you document a decision (e.g., "We're deferring MFA for alumni to fund research firewall upgrades"), you create defensible decision-making. You can show your decisions reflect good stewardship of resources and operate within approved constraints.
Savvy CISOs treat the interview process as their audit of the institution, not just the other way around.
The canary in the coal mine is liability insurance. Data confirms this instinct: 72% of CISOs now say they would not join an organization that does not offer Directors & Officers (D&O) liability coverage.
This isn't paranoia. This is professionalization.
Frustration with being a "figurehead" rather than a "risk executive" is a primary driver of churn. The average CISO tenure is just 18 to 26 months. That’s less than half the average tenure of other C-suite executives.
To survive as a CISO, you must test the institution’s appetite for reality before you take the job.
An institution that wants an advisor will ask, "What risks are we accepting by not funding this?" An institution that wants a scapegoat will ask, "Why isn't this dashboard green yet?"
93% of organizations have introduced policy changes in the last year to address CISO liability risks. If your institution hasn't, you're not just an employee. You're an insurance policy they haven't paid for.
For boards and hiring managers: if your CISO candidate doesn't ask about risk governance structure, they're naïve or desperate. The best candidates are interviewing you.
Higher education leadership is facing a crisis of capacity. Recent industry reports show that 84% of C-level executives in higher education describe their workloads as "excessive", creating a bottleneck where complex data cannot be processed.
I learned the concept of a one sheet summary early in my career from the "One Page Project Manager" (OPPM) methodology. The premise was brutal but true: if you cannot summarize your project’s current state and next steps on a single page, you do not understand your project as well as you think.
I applied the same philosophy to Cyber Heat Map, but built it for the specific complexity of cybersecurity planning in higher education. It uses a strategy of Layered Disclosure.
The Engine (The Rigor): Behind the scenes, we run a streamlined but rigorous assessment. We catalog adopted solutions, map them to the people and service providers supporting them, and analyze dependencies. The system then rank-stacks over 100 potential improvement areas, weighing current capabilities against compliance goals and risk mitigation targets.
The Decision Layer (The One Sheet): The output is the Improvement Recommendations report. It does not show the math. Instead, it shows the answer as the top weighted priorities, ranked by relative impact.
You educate your stakeholders about the rigor once, so they trust the summary forever. This allows you to present just the key information needed to decide, while the deep analysis data sits ready in your back pocket if a specific question arises.
If your security strategy can't fit on one page, it won't survive executive attention scarcity.
Complexity isn't rigor. It's confusion.
If you treat your roadmap as a "high score" leaderboard, you lose. If you treat it as a navigation system, you win.
You can game a planning system to look better. But gamed inputs produce useless outputs. If you lie about your current state, no tool can provide accurate recommendations, and you end up asking for funding for the wrong things.
The cost of this self-sabotage is quantifiable. Organizations lose an average of $12.9 million annually from poor data quality. 67% of leaders report not trusting the data they use for decisions.
Do the math for your institution: How much time does your team spend correcting roadmap and dashboard data each month, reconciling inventories, or explaining why last your priorities have changed? If it's more than a few hours per month, you're burning six figures on planning overhead instead of shoring up your security program.
This isn't about honesty in the moral sense. It's about operational utility.
I coach Cyber Heat Map users to treat the assessment as a living operational twin of their actual security program. When a project finishes, mark it complete. When a solution ages, flag it as "needs refresh."
Because the improvement recommendations update in near real-time, the incentive flips. You want the system to see your gaps because that’s how you generate the data you need to justify closing them.
You have a couple of options for implementing a portfolio structure to your security strategy:
Path A: The DIY Option. You can implement the methods outlined here using your existing project management tools or Excel. But be warned: 54% of organizations cannot track their KPIs effectively when managing projects manually. The "Excel Trap" is real. You end up managing the spreadsheet instead of the security program.
Path B: The Specialized Partner. You can leverage a purpose-built platform and support partner. This is where CampusCISO fits. We provide the "operational twin" engine pre-loaded with benchmarking data from 150+ higher education institutions. You get a set of recommendations backed by real data in just a few hours. Plus, you get expert support to validate your priorities.
Block out the time on your calendar (really schedule the meeting!) and then review your project list. If you have a list of things you hope to do rather than a funded portfolio of things you are doing, you need to pick a path.
Convince yourself first. If you are not 100% committed to killing the "traffic light" theater for your program status reporting, you are not ready for the friction of shifting to manage security as a portfolio.
Many CISOs are trapped by the belief that they must be infallible technical saviors. This "Superhero" identity is becoming a liability.
The pressure to be perfect is crushing. 66% of CISOs report facing excessive expectations, and two-thirds witnessed burnout in their peers this year.
To survive, you must kill the superhero and birth the risk advisor. You cannot fix everything, but you can assess everything.
On the organizational side, the friction is even harder to resolve because you often lack the authority to enforce your roadmap. You are trying to secure a network the CTO owns and cloud apps the business units bought.
Data confirms this isolation. 55% of organizations report that security and IT remain siloed, and 44% of security leaders struggle to manage risk because of challenging relationships with IT.
This is the Turf War Trap. When you try to prioritize projects, you are not just moving budget. You are threatening another leader's fiefdom.
If you lack the authority to win that fight, you retreat to "Traffic Light" reporting because it is safer to report on what you control than to expose risks you cannot fix.
The "living plan" is your treaty. By bringing the CIO and other IT leaders into the governance structure, you convert "security asks" into "institutional risks."
You stop fighting for your budget and start fighting for the institution's resilience.
For CIOs: if your CISO is still fighting turf wars for budget, you have a governance problem, not a security problem. If you are not actively considering cybersecurity choices across traditional budget lines, you’re preserving a status quo that neglects risk. Bring your CISO and their operational peers into institutional risk conversations or watch your security team burn out.
A roadmap that sits in a PDF goes stale the moment you hit "Save."
In fact, the World Economic Forum warns cybersecurity is entering an era of "unprecedented complexity." Nearly 60% of organizations report that geopolitical tensions alone have already forced changes to their cybersecurity strategy.
If your plan is not a living, continuously updated strategy, it is just an artifact of your last panic.
When leaders try to create planning tools with homegrown spreadsheets, the maintenance burden kills them. Many teams spend three or more months every year completing audits instead of supporting security operations work.
We built Cyber Heat Map to break that cycle by treating simplicity as a feature.
The friction is gone. You do not rewrite a 50-page document every cycle. You log in, toggle a project from "In Progress" to "Complete," or flag a tool as "Needs Refresh."
The reward is instant. The moment you update a single data point, your recommendations engine recalculates. You see in real-time how that one change moved your benchmark against peers. And what projects you should do next.
This isn’t a six-month consulting engagement that leaves you with a binder. It is a living system that lets you validate your approach in minutes.
It really should be that simple.
There is a misconception that showing complexity proves expertise. In reality, complexity signals confusion to a board and executives.
The data is damning: 70% of C-suite executives feel that security teams talk in technical terms without providing business context, leaving them unable to determine the actual risk exposure.
Even worse, while 84% of directors classify cybersecurity as a top business risk, only about half feel they understand it well enough to provide effective oversight.
This disconnect is why the "Traffic Light" approach thrives. It fills the void of understanding with pretty colors.
To break free, you accept that simplicity is a leadership discipline, not a technical failing.
Mastering the planning process allows you to maintain the complex view for yourself. This is the "operational twin" we discussed. But for the board, you translate that complexity into three simple variables: Risk, Resources, and Consensus.
Risk: "Here is the exposure we face."
Resources: "Here is the cost to reduce it."
Consensus: "Here is the decision we are making together."
When you do this, you stop asking for permission to do your job and start leading the institution's cyber risk strategy.
You will know you have escaped the Traffic Light Trap when:
This isn’t a theoretical transformation. It’s how strategic CISOs operate every day. The only question is whether you’re willing to make the shift from status reporter to risk advisor.

Start Your 30‑Day Diagnostic - $399
Build a data‑informed, board‑ready cybersecurity plan in 30 days.
Includes expert guidance, 30‑day access to the Cyber Heat Map® platform, and weekly group strategy sessions.
No long‑term commitment. Just results.
Secure your seat today.