Chris Schreiber
Higher-ed institutions can reclaim six-figure budgets by ditching overlapping licenses and fully deploying core controls. See how a layered heat map and peer benchmarks help campuses focus every dollar on the next high-impact move.
Your attack surface expands daily while your budget stays flat.
You purchase advanced AI detection platforms while legacy VPN accounts still use passwords. You fund threat hunting tools while backup systems point to the same vulnerable appliance.
This backwards approach explains why organizations waste money every year on unused security licenses.
The average enterprise now manages 76 separate security products. Yet only 10-20 percent of purchased capabilities ever get activated.
You’re building the penthouse while the foundation has cracks.
Picture walking into a room with 40 security products on the procurement ledger. Institution-wide MFA remains partially deployed. Some departments are not using the centralized backup services.
Organizations found that they only used 15 percent of the features included in their purchased solutions.
Twelve products performed log collection. Eight offered built-in MFA connectors. Half the “critical gaps” could be closed by enabling features already owned.
The room went silent. Then the objections started.
Network administrators insisted their log aggregator “caught anomalies faster.” The identity team argued their standalone MFA gateway offered “more flexibility” than the zero trust solution favored by the cloud infrastructure team.
But data doesn’t negotiate.
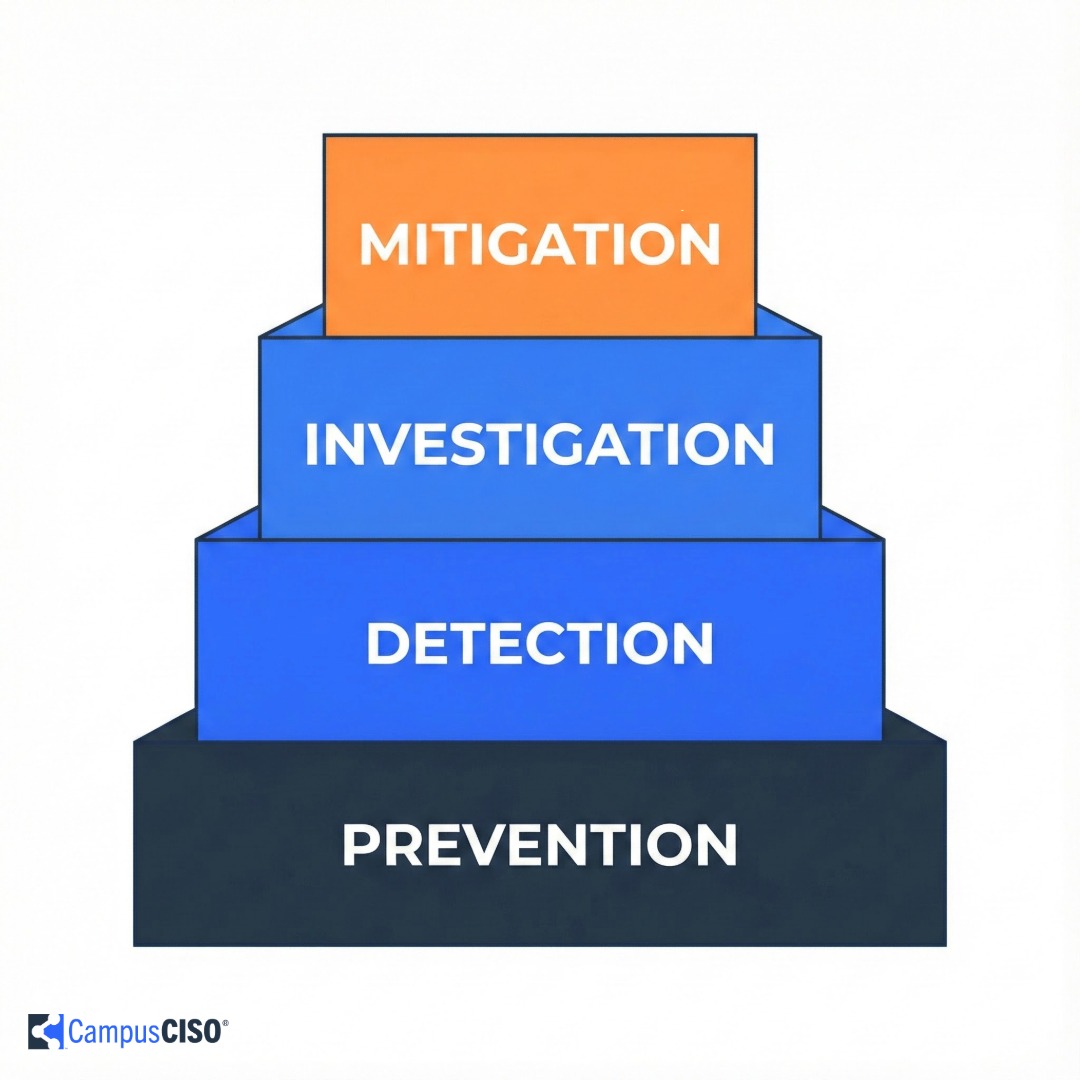
Imagine pouring sand into a wooden sandbox built in four layers.
Prevention forms the base. Patching, MFA, and immutable backups create your foundation.
Detection adds the second layer. Log collection, alerting, and basic analytics build upward.
Investigation brings correlation and root-cause analysis.
Mitigation crowns the stack with AI-driven hunting and automated response.
When you pour sand representing each control, physics reveals the problem. If lower layers remain half-filled, daylight appears beneath the top tier.
Advanced tools slip through foundational gaps.
You pay for features you cannot fully leverage because the supporting infrastructure doesn’t exist.
When teams document their “needed” advanced features that a point solution provides, our three most recent assessment projects show that only 22 percent survive scrutiny.
We found other solutions covered the rest of the “necessary” features that were used to justify one-off “best of breed” tools.
The bigger surprise comes from the gaps, not the overlaps.
Teams assume MFA protects everything. Yet legacy VPN accounts and many third-party SaaS admin logins still rely on passwords.
Central logging appears compliant. But retention caps at 30 days when new regulations require 12 months.
Backups seem immutable. Until you discover departmental file shares point to the same on-premise storage appliance that failed the ransomware test.
These blind spots create vulnerability while institutions continue to spend budgets on redundant tools.
Nobody wants to look careless when gaps surface in front of leadership.
The first emotion you see is fear. Someone realizes they’ve been reporting “MFA fully deployed” for two years when coverage actually sits at 60 percent.
Reframing transforms individual vulnerability into collaborative contributions.
Cybersecurity planning is driven by an ongoing improvement process instead of pass/fail audits. This aligns with the NIST Cybersecurity Framework focus on continuous improvement over one-time compliance.
Quantify the impact of your projects instead of assigning blame. What additional risks does this gap introduce? How much will it cost to fix this gap in hours or dollars?
Shift success metrics from perfection to progress. “MFA enforced on 25 percent of SaaS accounts this week, 50 percent next.”
This turns embarrassing discoveries into achievable improvement plans.
Present leadership with a one-page heat map showing capacity versus opportunity.
No red “failed audit” labels. The legend highlights where resources already exist and where gaps create risk.
Overlay an Improvement Priority Score for every potential project. Campus-wide MFA scores 92. The new AI hunting tool scores 34.
Executives see which investments deliver maximum risk reduction value per dollar.
Focus your discussions on future gains rather than past mistakes. Leaders champion rebalanced roadmaps while preserving credibility.
When security leaders join peer communities, the first surprise involves budget size.
Higher education devotes about 7 percent of IT spend to cybersecurity compared to 10 percent in private sector organizations.
That realization lowers the temperature. Everyone stretches limited resources.
The second shock comes from spending patterns. Many executives assume their peers are pouring money into AI-driven detection tools. But campuses spend most budget on people, backups, logging, and access control solutions.
Only thin slices remain for advanced analytics.
The conversation shifts from “We’re behind” to “Let’s trade playbooks for maximizing our 7 percent budgets.”
Organizations that maximize limited resources share one mindset shift.
They replace pass/fail compliance thinking with a continuous improvement focus.
Instead of asking “Did we pass the audit?” they ask “Are we measurably stronger this quarter than last?”
This requires live data and shared context. Platforms like Cyber Heat Map assign 0-to-100 Improvement Priority Scores, which help leaders see which actions deliver maximum risk reduction per dollar.
Peer benchmarks validate priorities against institutions facing similar budget constraints.
Progress becomes visible. Momentum gets celebrated. Budget conversations pivot from “We need more money” to “Here’s the next high-impact move we can fund right now.”
Expect forced budget realignments over the next 2-3 years.
Boards will question why the organization spends one-fifth of security dollars on perimeter gear when critical data lives in SaaS and cloud platforms.
Higher education already runs 88 percent of applications in cloud environments. Yet most leaders can’t show a similar investment in cloud security investments.
Economic pressure speeds up this pivot. Organizations using continuous improvement platforms can show why a firewall refresh gets deferred, so identity governance gaps are closed first.
Those operating on annual spending cycles will struggle to defend legacy budget levels.
Start with a rapid baseline assessment. Map every security product you own to the actual capabilities you’re using.
Cross-check high-priority gaps against solutions in your inventory. Most identity platforms include MFA. Most endpoint agents ship with EDR modules that are never activated.
Focus on always-on controls that reduce attack surface with minimal effort. Enable MFA on email, VPN, and SaaS logins. Deploy privileged access management tools to restrict attackers’ ability to spread laterally. Automate off-site, immutable backups. Patch externally facing systems within 15 days.
Retire redundant licenses at renewal and redirect savings to solutions that close high-impact gaps.
Publish a one-page roadmap with assigned owners and completion dates. Revisit quarterly to maintain momentum.
Your limited resources can deliver powerful protection when allocated strategically.
The question changes from “What new tool do we need?” to “Which solutions do we already own that closes this gap?”
That single shift routinely frees six-figure sums for foundational improvements.
Ready to see where your security roadmap stands? The 30-Day Strategy Sprint compresses weeks of evaluation into structured workshops that produce actionable roadmaps in hours.

Start Your 30‑Day Diagnostic - $399
Build a data‑informed, board‑ready cybersecurity plan in 30 days.
Includes expert guidance, 30‑day access to the Cyber Heat Map® platform, and weekly group strategy sessions.
No long‑term commitment. Just results.
Secure your seat today.