Chris Schreiber
Explore effective strategies for managing third-party risk in higher education institutions, balancing security needs with academic freedom and resource constraints.
Higher education institutions face third-party risk management challenges that would overwhelm even sophisticated corporate security teams—yet must address them with a fraction of the resources. Unlike corporations with centralized procurement and dedicated vendor risk staff, universities operate in a decentralized environment where individual departments, research groups, and faculty members make independent technology decisions without informing central IT or security teams.
This decentralized purchasing creates significant visibility gaps for CISOs. When combined with smaller security teams and tighter budget constraints, the situation demands a different approach to third-party risk management in academic settings.
Higher education CISOs navigate a unique environment shaped by several distinctive factors. The decentralized nature of academic institutions mirrors the complexity seen in large corporate conglomerates, but without the corresponding security resources. While a major corporation might employ a fully staffed vendor risk management team, university security teams must prioritize efforts because of strict budget and staffing limitations.
The approach to risk management itself differs. Corporate environments have embraced technology-driven solutions like automated vendor risk platforms and continuous monitoring tools. Universities often rely more heavily on manual processes, contractual language, and governance policies—introducing inefficiencies when dealing with the scale of vendor relationships common in academia.
Perhaps most significantly, universities must balance security requirements with academic freedom. Researchers, faculty, and students expect access to a broad range of digital tools and services, frequently resisting security measures perceived as restrictions on academic pursuits. This cultural dynamic creates challenges rarely encountered in corporate settings where security mandates face fewer objections.
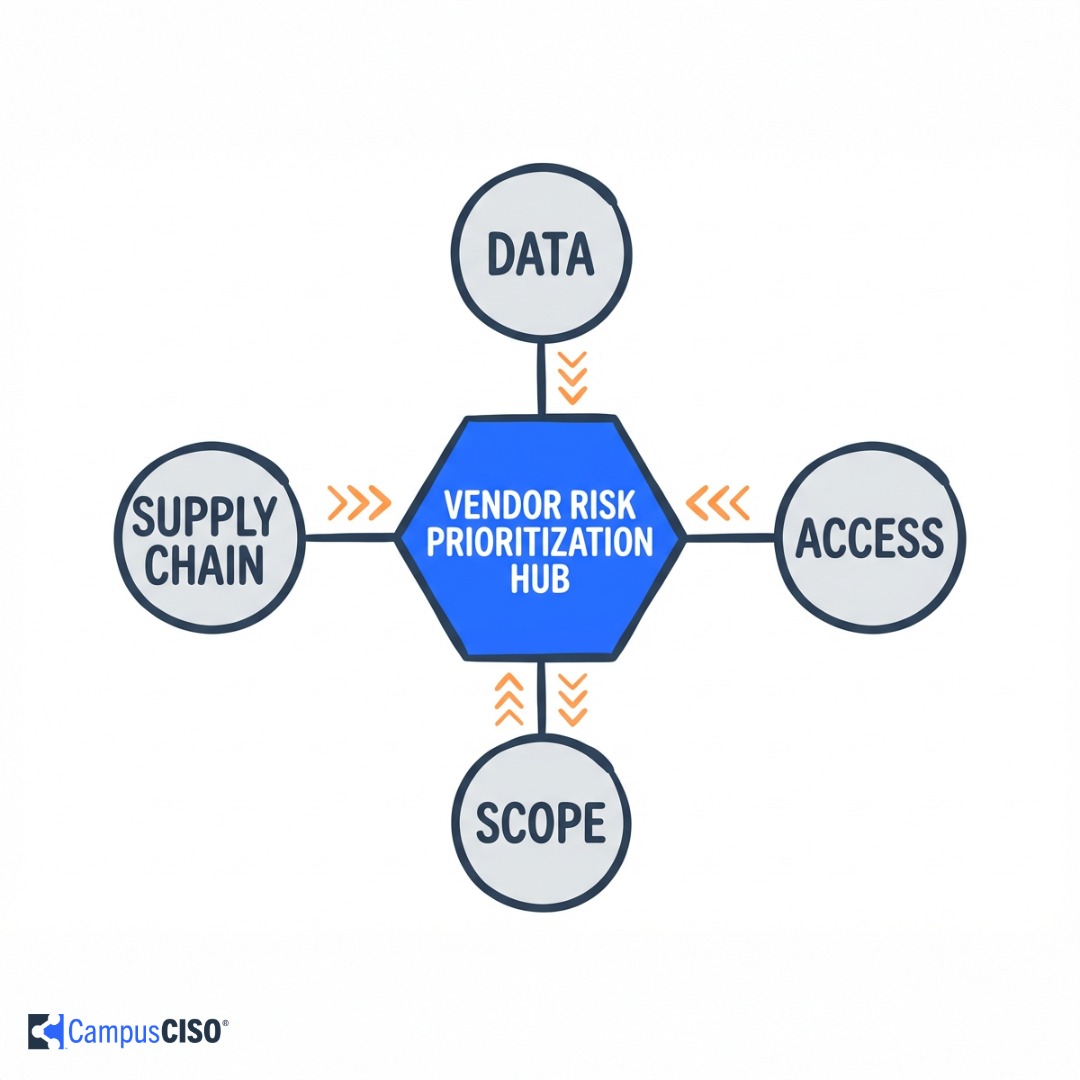
With limited resources, higher education CISOs cannot treat all vendors equally. A strategic, data-driven approach to vendor risk prioritization focuses efforts where they will provide the highest security impact.
Four key factors should guide vendor risk prioritization in academic settings:
1. Data Sensitivity: Vendors that process or store highly sensitive information require more rigorous assessment. This includes personally identifiable information (PII), financial data, protected health information under HIPAA, student records protected by FERPA, and research data, particularly those subject to federal export controls or grant requirements.
2. Access Level: Vendors with deep integrations into critical IT infrastructure demand heightened scrutiny. Identity and access management providers, cloud infrastructure platforms, remote monitoring tools, and security control systems can create institution-wide vulnerabilities if compromised.
3. User Scope: Vendors used institution-wide present higher risk exposure than those limited to a single department. Campus-wide systems like email, ERP platforms, and cloud storage services affect the entire institution. Meanwhile, broadly adopted shadow IT solutions, even if unofficial, may warrant assessment if widely used.
4. Supply Chain Dependencies: Vendors that rely on third-party infrastructure or services can expose institutions to indirect risks. The SolarWinds attack showed how a single compromised software provider can create widespread vulnerabilities across multiple organizations. Similarly, vendors that integrate with multiple other services through APIs or single sign-on create extended risk surfaces.
A tiered risk assessment framework provides a practical way to manage third-party risk in resource-constrained environments:
Tier 1 (High Risk): Critical vendors with access to sensitive data or infrastructure, such as ERP systems, cloud providers, IAM solutions, student information systems, and healthcare records, require comprehensive risk assessment. This includes security questionnaires (HECVAT), contractual security clauses, and continuous monitoring tools.
Tier 2 (Moderate Risk): Vendors handling some sensitive data but with limited scope or low privilege access, like learning management systems, email marketing tools, and HR systems warrant streamlined assessment, focusing on core security controls and compliance documentation.
Tier 3 (Low Risk): Vendors that do not store sensitive data and have minimal access, such as collaboration tools, free software used by faculty, and event management platforms, need only basic security review, potentially leveraging community assessments or past evaluations.
Automation can improve the efficiency and effectiveness of third-party risk management, particularly vital for resource-constrained higher education security teams. While the Higher Education Community Vendor Assessment Toolkit (HECVAT) provides a structured framework for security assessment, its manual nature creates inefficiencies. Strategic automation of specific tasks delivers the highest ROI for academic institutions.
Automated Vendor Risk Scoring & Continuous Monitoring: Rather than relying solely on vendor self-assessments like HECVAT, universities can implement automated risk intelligence platforms that continuously monitor vendors for security incidents, compliance changes, and potential breaches. Tools such as BitSight, SecurityScorecard, and RiskRecon evaluate external indicators of security posture—including exposed vulnerabilities, misconfigured cloud services, and data leaks on the dark web. This enables institutions to move beyond static, point-in-time evaluations toward dynamic, ongoing risk management.
Threat Intelligence & Dark Web Monitoring: Universities frequently lack resources to track whether vendors have experienced breaches or if institutional data has been compromised in underground forums. Automated dark web monitoring tools like Recorded Future and SpyCloud can alert institutions if credentials, intellectual property, or research data appear in illicit marketplaces. This provides real-time insight rather than waiting for vendors to disclose incidents—if they disclose them at all.
Automated Security Questionnaire Validation: One significant weakness of the HECVAT process is that vendor responses are self-reported and not always completed by the vendor’s actual security team. AI-driven tools like OneTrust, Prevalent, or ProcessUnity can validate responses by cross-referencing vendor answers against real-world security data, policy enforcement evidence, and compliance reports. Some platforms use natural language processing to flag vague or non-committal responses, allowing security teams to focus on high-risk vendors rather than manually reviewing every questionnaire in detail.
Automated Incident & Breach Notification Workflows: Many universities rely on vendors to voluntarily disclose security incidents—an unreliable approach. Automating vendor breach alerts via integrations with security intelligence platforms or APIs that pull from public disclosures ensures institutions receive timely notifications. These workflows can also trigger internal response actions, such as requiring vendors to submit updated security documentation or escalating concerns to procurement and legal teams.
Contractual Compliance & SLA Enforcement: Security clauses in vendor contracts often lack effective enforcement mechanisms. AI-powered contract management platforms can scan vendor agreements to ensure compliance with cybersecurity requirements and generate automated reminders when vendors must provide updated security attestations or compliance documentation. This reduces reliance on manual check-ins and ensures contractual security requirements remain enforceable throughout the vendor lifecycle.
Cross-functional collaboration represents a critical success factor for third-party risk management in higher education. Effective models integrate security reviews into existing institutional processes, rather than creating isolated security checkpoints.
Procurement & Finance: Procurement teams serve as the first line of defense in identifying vendor relationships. Embedding security reviews into procurement workflows closes visibility gaps and ensures security consideration before contracts are signed. Practical approaches include embedding security screening questions in standard purchasing forms, assigning designated security liaisons who meet regularly with procurement, and integrating security evaluation criteria into RFPs for larger acquisitions.
Legal Teams: Legal departments help codify security expectations within contracts, reducing institutional liability and ensuring vendors meet baseline requirements. Working with legal to develop standard cybersecurity requirements for vendor contracts creates consistency. Legal can push back on weak security terms during negotiations and help enforce contractual obligations over time, such as requiring vendors to submit annual security updates.
Distributed IT Teams: Many universities have decentralized IT groups embedded within individual colleges, research departments, and administrative units. These teams often select and manage their own technology vendors, making their participation in risk management essential. Position security as a partner in making safe technology choices rather than a blocker, provide guidance on recognizing vendor risks, and ensure distributed IT groups contribute to institution-wide vendor inventory.
Data Governance & Compliance: Universities handle regulated data across multiple domains—student records under FERPA, financial data under PCI DSS, research data under federal export controls. Align third-party risk assessments with existing data classification and compliance programs to ensure vendors handling sensitive data receive scrutiny. Engage research compliance teams to help monitor risks associated with third-party research tools and cloud platforms.
Incident Response & Security Operations: A well-integrated third-party risk program extends beyond pre-purchase assessment to ongoing monitoring and incident response. Ensure security teams receive real-time alerts if vendors experience security incidents and conduct joint incident response exercises that include third-party breach scenarios, ensuring all stakeholders understand their roles.
The University of Central Florida shows effective cross-functional collaboration through its comprehensive Vendor Risk Management program (https://infosec.ucf.edu/risk-and-compliance/vrm/). UCF requires any department considering contracts with third-party providers that involve university data to submit detailed information about the proposed vendor. The Information Security Office reviews these submissions and produces formal assessment reports summarizing potential risks and recommendations. These reports require review and signature by business and data owners, creating shared accountability across the institution.
For higher education CISOs, formalizing third-party risk management with limited resources, a structured, incremental approach yields better results than attempting to assess every vendor. Focus on building institutional support, establishing risk-based policies, and targeting high-impact areas first.
Build a Cross-Functional Coalition: The CISO cannot manage third-party risk alone. Identify key stakeholders from procurement, finance, distributed IT groups, legal, data governance, and compliance. Establish a standing working group to oversee third-party risk policies and approvals. Gain buy-in by framing security as an enabler of institutional trust and compliance rather than an administrative burden.
Define and Formalize a Third-Party Risk Policy: Higher education institutions operate with strong governance structures, so a documented policy helps align stakeholders and set expectations. Develop a policy that defines risk factors, vendor categorization criteria, and required security assessments per tier. Align with existing institutional governance and make policies actionable—avoiding complex processes that discourage compliance.
Prioritize High-Risk Vendors First: Focus on vendors that could cause the most damage if breached: ERP systems, student information systems, cloud platforms, IAM solutions, research data platforms handling controlled unclassified information, and campus health services vendors. Implement a tiered model where high-risk vendors require full assessment, while low-risk vendors undergo only basic due diligence.
Embed Security Into Procurement: Since many IT purchases happen outside central IT control, embedding security into procurement ensures early risk detection. Work with procurement to integrate security risk questions into vendor intake forms, require HECVAT or equivalent security assessments for major IT purchases, and create simple security checklists for distributed IT teams.
Establish a Vendor Inventory: Many institutions lack visibility into which vendors are in use, making risk assessment difficult. Compile a basic inventory from procurement records, financial systems, and software asset management tools. Identify which vendors process sensitive data or integrate with critical infrastructure. Use free or low-cost monitoring tools to track security incidents related to vendors.
Implement Quick Wins with Strategic Automation: Small security teams cannot manually track every vendor. Use vendor risk scoring tools if budget allows. Set up Google Alerts or open-source threat feeds to track public security incidents for major vendors. Automate breach notification alerts using public breach databases.
Educate & Engage Distributed IT Teams: In decentralized environments, distributed IT groups often onboard vendors independently. Provide basic security training on third-party risk, offer easy-to-use security guidance, and position security as a partner rather than a blocker.
Plan for Long-Term Maturity: A comprehensive third-party risk program develops over time. Start with manageable steps: establish governance, prioritize high-risk vendors, and embed security in procurement during the first six months. Build a complete vendor inventory, introduce automation, and strengthen contract security clauses in months 6-12. Implement continuous monitoring and expand assessments beyond high-risk vendors after the first year.
Higher education possesses a unique advantage in third-party risk management: the sector shows remarkable collaboration and willingness to share assessments, best practices, and benchmarking data. This collaborative spirit helps institutions overcome resource constraints through collective effort.
REN-ISAC Community Broker Index: The Research & Education Networks Information Sharing & Analysis Center maintains a central repository of completed vendor security assessments, allowing institutions to reuse evaluations instead of duplicating effort. This saves significant time and reduces vendor fatigue from repetitive questionnaires. When engaging new vendors, first check if they have already submitted a HECVAT to the Community Broker Index.
Cloud Security Alliance STAR Registry: The Security, Trust, Assurance and Risk program maintains a publicly accessible registry documenting security controls of major cloud vendors. This resource helps universities quickly evaluate cloud provider security postures before conducting their own assessments and allows comparison between providers to aid procurement decisions.
EDUCAUSE Cybersecurity Program: This higher education IT organization offers benchmarking tools, case studies, and peer discussion forums addressing third-party risk management. Their Cybersecurity & Privacy Community Group facilitates knowledge sharing about vendor risks, security incidents, and mitigation strategies.
Regional Assessment Consortiums: Many universities form smaller regional working groups to share vendor security evaluations. Some create “HECVAT user groups” where schools collectively assess vendors of interest, while certain state university systems collaborate on security evaluations for shared contracts.
To maximize value from these resources, encourage vendors to take part in industry programs, use community benchmarks to validate internal approaches, collaborate with peer institutions on high-impact vendors, and monitor vendor risk signals across the community. If a vendor experiences a breach at another institution, proactively assess your own exposure before official disclosures.
Higher education CISOs face a unique challenge: ensuring security without stifling innovation and academic pursuit. Unlike corporate environments where security policies are strictly enforced, universities thrive on experimentation and academic freedom, which can lead faculty, researchers, and students to adopt technologies independently.
Rather than acting as gatekeepers blocking technology, effective CISOs focus on collaboration, education, and risk-adjusted flexibility. This ensures security enables academic pursuits rather than hindering them.
Shift the narrative from security as an obstacle to security as an enabler. Frame security measures as tools for protecting research integrity and ensuring operational continuity. Engage faculty early when considering new tools rather than after adoption, making security part of the decision process. Highlight real-world examples like the 2020 Blackbaud ransomware attack, which compromised donor and student records at multiple universities, to create support without fear mongering.
Implement a tiered, risk-based approach that recognizes not all solutions pose equal risk. Allow lower-risk tools to be used with minimal friction while focusing security reviews on high-risk vendors. Build collaborative review processes that provide faculty flexibility while giving security teams necessary visibility. Establish clear technology approval processes without unnecessary bureaucracy and offer security consultations to understand needs rather than forcing lengthy reviews upfront.
Integrate security into procurement and IT registration processes to improve awareness. Require new software and cloud services to be registered during procurement, ensure procurement teams include security for high-risk purchases, and offer pre-approved vendor lists for common tools.
Educate faculty on good security practices through role-specific training on topics like safe AI use for research and secure vendor selection. Offer security office hours where faculty can discuss technology needs in a non-confrontational setting. Develop quick-reference security guides explaining how to evaluate vendor security, what data types require extra precautions, and what funding agencies require for data protection.
The third-party risk landscape continues to evolve, with interconnected, complex, and increasingly opaque technology ecosystems creating new challenges for higher education institutions. CISOs should prepare for several key developments:
Fourth-Party and Supply Chain Risk: Risk extends beyond direct vendors to their subcontractors, cloud platforms, and infrastructure providers. Recent supply chain attacks like SolarWinds show how a single compromise can cascade across multiple institutions. Require vendors to disclose critical dependencies, use risk intelligence tools to map vendor ecosystems, and establish contract requirements for vendors to disclose security incidents involving their supply chain partners.
Regulatory Pressures: Governments and regulatory bodies continue tightening third-party risk compliance requirements for higher education, particularly for research data, student privacy, and financial systems. Institutions handling controlled unclassified information, federal research grants, or healthcare data face stringent security requirements. Monitor updates to compliance frameworks like NIST 800-171 for research security, include contractual compliance requirements in vendor agreements, and ensure new contracts include mandatory security attestations for high-risk vendors.
AI-Powered Vendor Solutions: Vendors increasingly embed AI capabilities into their software, sometimes without transparency about how AI processes, stores, or learns from institutional data. This creates data leakage, biased decision-making, and compliance risks if models train on sensitive data. AI-driven fraud and sophisticated phishing make third-party impersonation more dangerous. Require vendors to disclose AI usage details, develop AI governance frameworks, and monitor for AI-generated security threats.
Growing Complexity of Risk Management: Many institutions lack budget for enterprise-class vendor risk management tools, while manual HECVAT reviews grow too slow and resource-intensive to keep pace with new vendors. Prioritize automation where possible, use shared community resources to reduce assessment duplication, and shift from one-time assessments to continuous monitoring approaches.
Cyber Insurance Pressures: Insurance providers increasingly require rigorous third-party risk assessment. Institutions that fail to assess vendors may face premium increases or coverage denial. Meanwhile, some vendors push liability onto institutions through contract language. Review vendor liability clauses, engage with cyber insurance providers to understand how vendor security practices impact coverage, and negotiate specific breach notification timelines in contracts.
One significant pitfall in third-party risk management—especially in resource-constrained environments—is mistaking busywork for actual risk reduction. Complex processes, lengthy questionnaires, and contractual clauses create the appearance of strong security without improving institutional protection.
Higher education CISOs should focus on making risk understandable for leadership by shifting from activity metrics (“we completed X vendor assessments”) to risk trends and institutional impact. Demonstrate progress in stages, from establishing vendor inventory to implementing automated monitoring. Measure impact rather than just activity by tracking risk level shifts, vendor incident management effectiveness, and mitigation plan implementation.
For CISOs feeling overwhelmed by complexity, two foundational principles provide a path forward. First, start small, build repeatable processes, and expand gradually. Prioritize highest-risk vendors first, standardize assessment approaches, and use simple tools before investing in sophisticated platforms. Second, leverage existing resources and build collaborative culture by embedding security into vendor onboarding, using community resources, and making visibility a priority.
Progress matters more than perfection. By focusing on high-impact areas, establishing repeatable processes, and leveraging collaboration, higher education CISOs can strengthen third-party risk management without exhausting limited resources. This practical, phased approach ensures institutional security while supporting the innovation and academic freedom that define university environments.

Start Your 30‑Day Diagnostic - $399
Build a data‑informed, board‑ready cybersecurity plan in 30 days.
Includes expert guidance, 30‑day access to the Cyber Heat Map® platform, and weekly group strategy sessions.
No long‑term commitment. Just results.
Secure your seat today.