Chris Schreiber
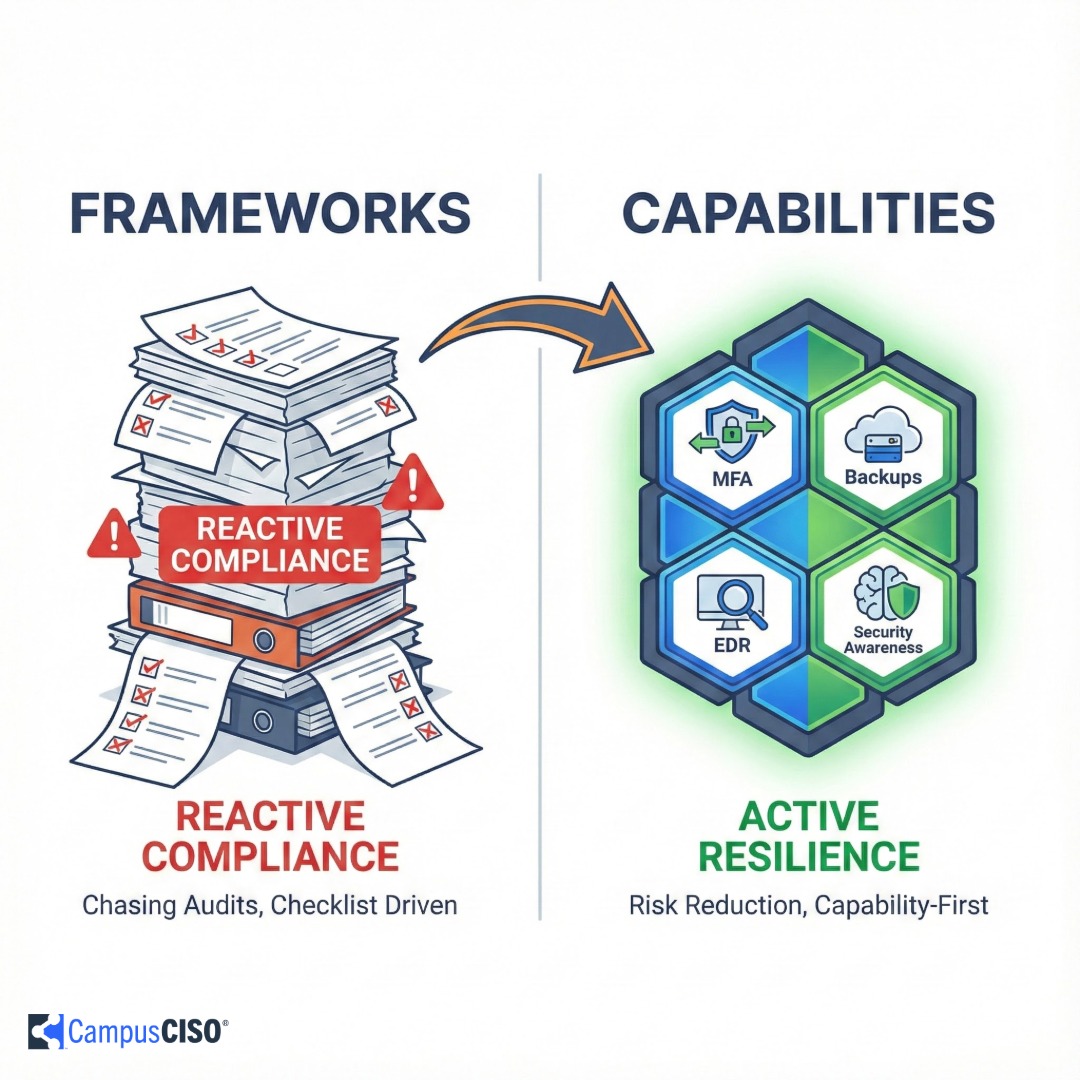
Higher education leaders often get stuck chasing audits and checklists, leaving real risks unaddressed. A capability-first approach shifts focus to investments like MFA, backups, and monitoring, helping institutions build resilience within limited budgets. With clearer priorities and defensible plans, leaders can show progress to boards while meeting compliance as a natural outcome.
Early in my CISO career, I walked into a board audit committee ready to discuss risk, priorities, and a roadmap.
Within minutes, the conversation shrank to closing findings about password rotation and vulnerability scans.
In the same quarter, my team spent more time on vendor questionnaires than on rolling out multifactor authentication. I wrote one line in my notebook: “We need a better way.”
The real problem hit me. Audits and frameworks were steering strategy, while material risks went unaddressed.
That moment changed how I think about cybersecurity strategy.
I stopped treating every finding as an isolated fire drill. Instead, I began treating cybersecurity like an investment discipline.
Capability becomes the engine. Compliance becomes the odometer.
One tells you how far you’ve gone. The other actually moves you forward.
This distinction matters more than most leaders realize. Only 48% of public sector organizations plan to increase their cybersecurity budgets in 2025. When dollars are scarce, every investment must count.
Capability-first means we plan around enduring abilities, not isolated controls. Think of it as portfolio management.
Controls are individual stocks or bonds. Capabilities are the asset class that drives long-term resilience.
When you ask a university CIO or IT director two simple questions, everything shifts:
If ransomware hit on a long weekend, which capabilities would you want already working before you ever opened an audit?
Given budget constraints, where should you allocate the next dollar to minimize current risk, not just resolve an audit observation?
These questions naturally pivot the discussion to capabilities like identity coverage, backup and recovery, and monitoring tools.
The Cyber Heat Map® platform makes this concrete. It organizes your current state into a comprehensive Improvement Recommendations Report that surfaces strengths, gaps, and prerequisites. You can quickly identify your top potential projects based on Improvement Priority, which I define as expected risk reduction adjusted for relative cost and effort, with 0-100 Improvement Priority scores assigned to every potential project.
Audits and frameworks aren’t the enemy. They’re retrospective tools that measure what already happened.
I honor the reality higher education leaders live in. NIST, PCI, and CIS frameworks provide valuable structure. But 41% of companies lack the tools to enforce the policies they’ve written in response to compliance requirements.
The problem isn’t the frameworks themselves. It’s letting checklists steer the wheel.
Good security is good for the organization regardless of which framework you reference. If you build the strongest program you can within the constraints of your budget, staffing, and culture, compliance follows as a byproduct.
Here’s how this played out with a state university CIO who asked me to stand up a dedicated NIST 800-171 task force for a single research contract.
They already had PCI and HIPAA programs. Staff were updating three sets of checklists and chasing one-off audit fixes. Little time went to MFA coverage, endpoint security improvements, or backup and recovery.
It was busy, not better.
I asked him to step back and apply a capability-first lens. We opened the Cyber Heat Map platform, reviewed the Improvement Recommendations Report, and let the picture drive the plan.
The report pointed to identity governance and MFA coverage, EDR on every workstation and server, centralized logging with basic alerting, and tested backup and recovery.
We applied those investments across the entire university, not just the research enclave.
Two practical shifts unlocked momentum. We consolidated overlapping tools to free budget, and we sequenced work so prerequisites were in place before advanced projects.
Within two quarters, the board had a plain, defensible narrative. The research program satisfied 800-171, and PCI and HIPAA findings dropped because the same new capabilities underpinned all three.
Compliance became the odometer again. Capability was the engine.
Working with 140+ higher education leaders over the years has shown me the same pattern everywhere I go.
Leaders who chase audit findings stay stuck in reactive mode. Leaders who focus on building actual capabilities get ahead of problems and show progress to their boards.
Universities and colleges operate in a perfect storm. You have students, faculty, researchers, and staff all needing different levels of access. You have federal research contracts with strict requirements sitting next to academic freedom principles. These actions must occur within budgets that always feel inadequate for the scope.
But their starting points vary. Some examples from CampusCISO customers include:
University CISO, decentralized identity: Pain points include uneven adoption of MFA, shadow IT in research, privileged sprawl, and patching gaps. The top priorities often become identity governance with universal MFA, endpoint baselines and EDR across all devices, privileged access management, centralized logging for identity and key apps with basic alerting, and tested backup and recovery for research data.
Community college IT director, resource constraints: Pain points include a small team, diverse student device management, aging infrastructure, and limited security tools. The top priorities often become consolidated security tools, MFA for email and student information systems, endpoint management across BYOD and lab computers, backup and recovery with regular testing, and basic security monitoring for student data systems.
The capability model behind Cyber Heat Map is intentionally agnostic. It looks at relative cost and effort, the way capabilities support each other, and your current state, then ranks what to do next using Improvement Priority.
As conditions change, you update answers. If something that was solid now needs attention, mark it “Needs Refresh,” and the list reorders.
The pattern holds across institutions because capability, not a checklist, is what actually moves the program.
Through the CampusCISO Strategic Operating System and the Cyber Heat Map® platform, I help higher education leaders make this capability-first shift concrete and sustainable.
The platform combines structured assessment, data-driven prioritization, and live expert guidance in one workflow designed for resource-constrained institutions. You complete in hours what traditional consulting engagements take weeks to produce.
What makes this different? Direct access to founder-led guidance, peer benchmarking across 140+ higher education leaders, and a mapped library of 1,300+ security solutions that connects capability gaps to real-world options.
Clarity matters when you’re briefing a board or budget committee. Only 23% of organizations say their boards understand their cybersecurity metrics.
The Cyber Heat Map platform is the right fit for a capability-first conversation. It organizes your answers into comprehensive reports that surface strengths, gaps, and prerequisites with clear 0-100 Improvement Priority scores for every potential project.
This scoring delivers a straightforward, defensible process for allocating resources.
The click happens when the Improvement Recommendations Report appears. We fill in the Cyber Heat Map platform together, and within minutes they see strengths, gaps, and sequencing with clear Improvement Priority scores.
I often hear, “Now I can see it.”
The noise of audit findings and tool preferences quiets down because the tradeoffs are visible. They notice prerequisites that were easy to skip in a checklist world that show up as foundational for advanced capabilities they want to deploy.
The second click is the Improvement Recommendations Report. Instead of debating maturity numbers, we look at Improvement Priority. The list is plain, defensible, and ready to brief in ten minutes.
A CIO can point to items one through five, explain why they lead, and show how they also satisfy multiple framework requirements as a byproduct.
The lasting shift is the cadence. Teams stop writing plans that gather dust.
When they complete a project, or when something solid drifts, they update a single value, including “Needs Refresh,” and the platform recalculates. The next best projects rise to the top without forming a committee or adopting a new tool.
I coach leaders to treat the Cyber Heat Map platform as a living plan. The rhythm is simple, and it sticks because it respects higher education time and budget realities:
Week 0: We baseline. We complete the assessment honestly, generate the Improvement Recommendations Report, and brief leadership on what we’ll do first based on Improvement Priority.
Monthly, 30 minutes: We reopen the platform. We update any items that moved, mark anything that has drifted as Needs Refresh, and confirm progress on the Improvement Recommendations Report. No slide deck, just the report on screen and clear owners.
Quarterly re-baseline: We refresh the assessment, update answers that changed, and let the new improvement recommendations recalculate. Two rules guide the conversation: prerequisites before advanced projects, and consolidate to reinvest when overlap appears.
Trigger events: If a major incident, audit, or acquisition occurs, we run an out-of-cycle refresh. Ten minutes of editing yields a revised, defensible plan.
At six to twelve months, leaders usually report fewer ad hoc debates and faster agreement on tradeoffs. The plan remains lean and credible because it’s always current.
The biggest hurdle is letting go of the idea that a multi-year, framework-mapped plan is the strategy. In the higher education sector, that feels safe, but it locks leaders into yesterday’s assumptions.
I coach them to replace a fixed plan with a living plan, where success is measured by capability adoption and sequencing, not by the weight of a binder.
After two cycles, the mindset change sticks. Leaders see that capability-first planning reduces debate, clarifies tradeoffs, and keeps compliance as a byproduct, not the driver.
Before you open the Cyber Heat Map platform, make one mental shift: treat cybersecurity planning as resource allocation across capabilities, not as checklist completion.
The platform is a planning tool for budget owners, not a GRC system. It focuses on capability prioritization and investment guidance rather than comprehensive compliance tracking.
It will help you decide where your next dollar or hour should go, and why.
Enter with three commitments. First, be candid about your current state across silos, including items that need to be refreshed. Second, focus on capabilities that raise resilience for the whole organization, not one-off fixes for a single audit. Third, let prioritization follow Improvement Priority.
If you hold that mindset, the deliverables will click. The Improvement Recommendations Report shows strengths, gaps, and sequencing in plain view. The Improvement Recommendations list gives you a defensible, cross-functional plan you can brief in ten minutes.
This method has helped over 140 higher education leaders escape planning cycles and make progress.
When you’re ready to try a capability-first approach to planning, remember to stay focused on building enduring capabilities and not just check boxes. You’ll gain a roadmap that makes sense to you, your team, and your board.
Ready to make the shift from compliance checklists to capability-first planning? The CampusCISO Guided Membership can guide your institution through this transformation with personalized strategy support and the full Cyber Heat Map platform. For those who want to experience this approach firsthand, the 30-Day Cyber Strategy Diagnostic offers a low-cost way to complete your first assessment and get 30 days of platform access to see how capability-first planning works for your specific environment.

Start Your 30‑Day Diagnostic - $399
Build a data‑informed, board‑ready cybersecurity plan in 30 days.
Includes expert guidance, 30‑day access to the Cyber Heat Map® platform, and weekly group strategy sessions.
No long‑term commitment. Just results.
Secure your seat today.