Chris Schreiber
Help desk device enrollments and automated student verifications are giving criminals valid credentials. Scattered Spider MFA bypass and bot student fraud expose process gaps that firewalls miss. Learn steps to build identity-first protection, continuous monitoring, and accountable training.
Your help desk just enrolled a device controlled by a criminal.
The call sounded routine. A frustrated executive needed to add a second device to their account for an upcoming trip. The support technician followed protocol, verified basic information, and registered the new device within minutes.
What they actually did was hand over complete account access to the Scattered Spider threat group.
The FBI’s recent warning about this group’s expansion from retail to airline targets reveals something crucial. These attackers don’t break code. They break processes.
The same vulnerability appears in a completely different context. California community colleges report that 34% of aid applicants are likely fraudulent. Bot students create synthetic identities, pass automated verification checks, and collect financial aid refunds before disappearing.
Two different industries. Two different attack methods. One shared weakness.
Both Scattered Spider and bot student operators exploit the gap between static verification and continuous identity assurance.
In airline attacks, criminals convince help desk staff to register attacker-controlled devices. Once enrolled, legitimate multi-factor authentication codes flow directly to the intruder. The MFA system works perfectly. The enrollment process fails completely.
In higher education fraud, criminals submit real stolen identities that pass database checks. Social Security numbers match. FAFSA forms validate. Financial aid systems see legitimate students and disburse funds accordingly.
The verification happens once. The exploitation continues indefinitely.
This represents a fundamental shift in how attacks work. Criminals no longer need to break through technical defenses. They walk through human-managed processes that assume good faith.
Your firewall can’t stop a properly enrolled device. Your identity database can’t flag a real Social Security number. Your MFA system can’t distinguish between a legitimate user and someone who convinced your help desk to add their phone.
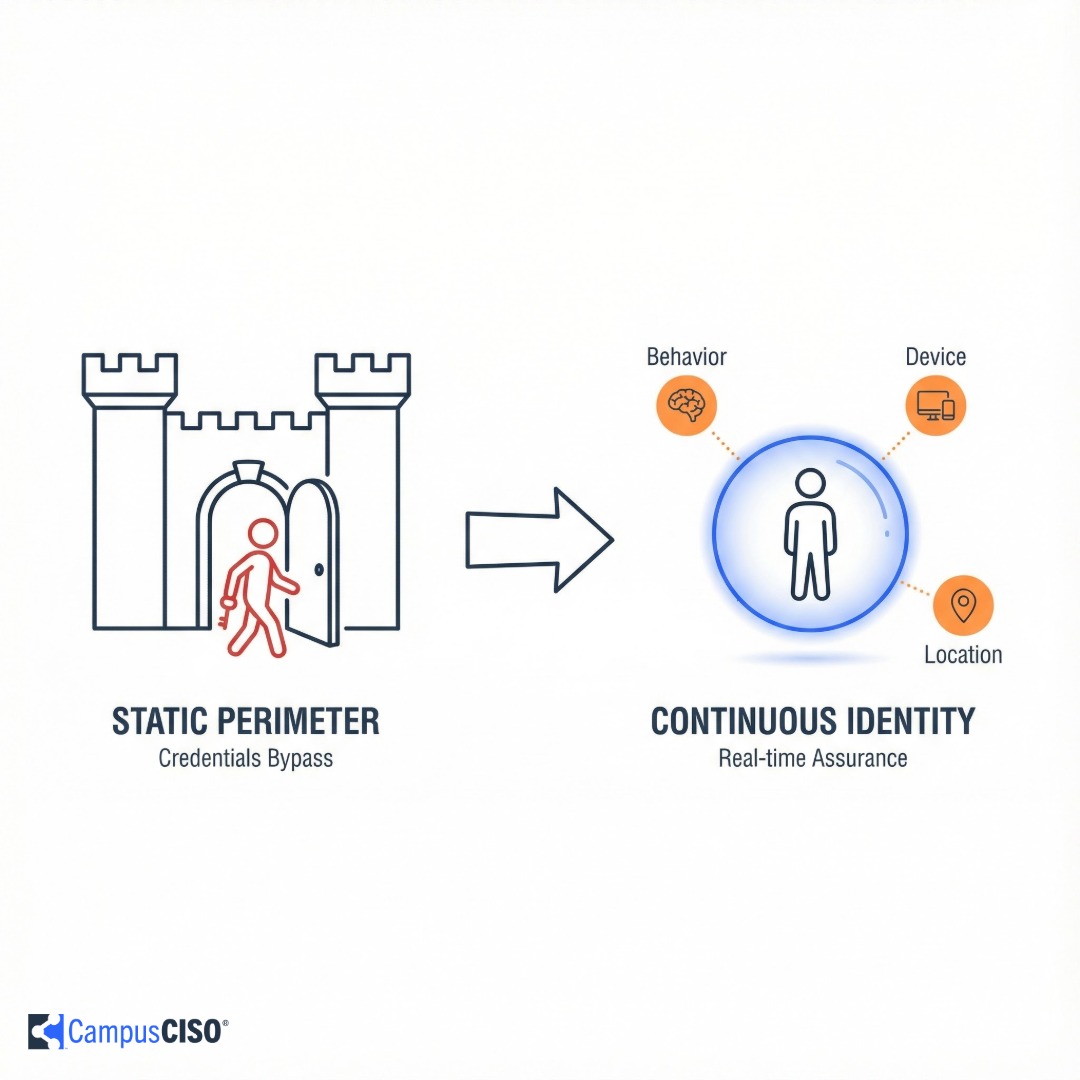
Most security programs focus on the wrong perimeter.
Twenty years ago, most institutional data sat in campus data centers. Building walls around those centers made sense. Today, your data lives in cloud services you don’t directly manage.
Despite this, many institutions still allocate security budgets as if the old perimeter exists. They pile more controls around empty buildings while attackers walk through the front (cloud) door with valid credentials.
The numbers prove this approach fails. Cisco Talos found MFA bypass techniques in nearly half of all security incidents during Q1 2024.
The problem isn’t the technology. MFA blocks most automated attacks when properly implemented. The challenge lies in the enrollment, management, and monitoring processes around that technology.
Attackers know this, and they’ve shifted their focus accordingly. Instead of finding ways to “hack” the systems, they convince help desk staff. Instead of exploiting software vulnerabilities, they exploit process gaps.
These attacks create damage beyond immediate financial losses.
When the University of Michigan suffered a cyber intrusion, they disabled internet access across all three campuses for three days. Faculty couldn’t teach. Students couldn’t submit assignments. IT staff worked around the clock to rebuild trust in systems that had “always worked.”
The attack exposed data on 230,000 people and disrupted the first week of classes. Technical recovery took days. Trust recovery took months.
Bot student fraud creates similar ripple effects. Fake enrollments consume financial aid that legitimate students need. Faculty waste time grading AI-generated assignments. Administrators spend resources investigating suspicious patterns instead of supporting real academic programs.
Moody’s Ratings now factors cybersecurity incidents into institutional credit assessments. What once seemed like an IT problem now affects borrowing costs and capital projects.
Organizations that recognize this shift early gain a significant advantage. Those that wait for their own wake-up call pay a much higher price.
To strengthen your security posture, start by asking how you know who someone really is.
This goes beyond checking credentials once during enrollment. It requires continuous identity assurance throughout the entire account lifecycle.
Risk-adaptive access challenges logins that exhibit unusual patterns. Device location, login velocity, and behavioral signals all contribute to ongoing verification. A credential that works from New York at 2 PM shouldn’t automatically work from Moscow at 2:05 PM.
Identity threat detection monitors for privilege escalation, dormant accounts that suddenly activate, and unauthorized device enrollments. The goal is to catch process exploitation before it succeeds.
Lifecycle hygiene automates rapid de-provisioning when students withdraw or staff roles change. Many bot student schemes exploit accounts that should have been disabled weeks earlier.
Budget reallocation can shift some funds from firewall upgrades to identity governance platforms and behavioral analytics tools. CIOs must consider total risk, not just traditional budget allocations among different IT teams.
President Michael V. Drake’s cybersecurity mandate required every University of California campus to achieve 100% employee training completion by May 2025. Interim reports show that 90% of faculty and staff have already finished role-specific security training.
The key insight: they made security awareness a presidential-level mandate, not an IT project.
Campuses must prove completion rates to maintain compliance. Deans and CFOs see their own unit’s status on public dashboards. Cyber training became a performance metric like accreditation requirements.
This approach works because it addresses the human element that attackers actually exploit. Help desk staff who complete social engineering simulations recognize suspicious device enrollment requests. Admissions staff who understand synthetic identity fraud spot unusual application patterns.
The cost remains modest. Micro-learning modules take 2-5 minutes monthly rather than hour-long annual sessions.
The impact scales exponentially. By training your users, you can extend the reach of your security efforts.
You don’t need the University of California’s resources to implement identity-first protection.
Start with leadership commitment. Ask your president to send a campus-wide message stating that cybersecurity training is part of everyone’s job. This costs nothing but elevates the program from “IT reminder” to institutional priority.
Inventory your current identity flows. Document every system, privileged account, and third-party connection. You can’t protect what you can’t list.
Map device enrollment processes across all systems. How does someone add a phone to their MFA account? Who approves additional devices? What verification happens beyond basic information checks?
Implement behavioral monitoring for unusual patterns. Identical IP addresses across multiple accounts, device fingerprints shared between users, and rapid privilege escalation all signal potential compromise.
Establish time-boxed governance. A 12-month fraud task force with representatives from admissions, financial aid, IT, and security can focus on measurable outcomes without getting lost in committee structures.
Measure completion publicly. Create simple dashboards showing each department’s training completion rates and simulated phishing results. Reputational incentives often work better than financial ones in academic environments.
Think of identity-first security like TSA PreCheck rather than airport perimeter fences.
Every passenger still crosses the airport boundary, but the real protection comes from continuous identity vetting. Travelers who pass background checks move through security more efficiently.
With TSA PreCheck, 99% of vetted passengers move through security in under 10 minutes because the system knows who they are.
Your security program should work the same way. Known users with verified devices and normal behavioral patterns get seamless access. Unusual requests trigger additional verification steps.
The goal isn’t to slow down legitimate users. It’s to create friction for attackers who rely on process exploitation.
The threat landscape gets more complex every year. Unfortunately, many security budgets haven’t grown to match.
Attackers can buy phishing toolkits on Telegram instead of writing custom exploits. They use social engineering scripts that target help desk processes instead of writing custom malware.
Organizations that continue investing primarily in traditional perimeter and network controls will find themselves defending empty datacenters while attackers easily access SaaS and cloud resources with valid credentials.
Successful institutions will define identity as their new security perimeter. They’ll invest in continuous verification, behavioral analytics, and human awareness rather than just adding more walls around systems that no longer contain their most valuable assets.
Your data moved to the cloud. Your users work remotely. Your students learn online.
Your security perimeter needs to match this new reality.
The choice is simple: adapt your approach to match today’s threats, or wait for your own ransomware moment to force the change.
The attackers aren’t waiting. Neither should you.

Start Your 30‑Day Diagnostic - $399
Build a data‑informed, board‑ready cybersecurity plan in 30 days.
Includes expert guidance, 30‑day access to the Cyber Heat Map® platform, and weekly group strategy sessions.
No long‑term commitment. Just results.
Secure your seat today.